EagleSpy V5 Technical Breakdown

A Threat Intelligence Overview of EagleSpy and EagleSpy v5:
Introduction to EagleSpy Malware
EagleSpy V5 is an emerging Android malware strain that has attracted the attention of cybersecurity researchers due to its modular structure, stealth capabilities, and presence in several real-world malicious campaigns. This report serves exclusively as an analytical and educational overview for SOC teams, mobile security analysts, and digital forensics researchers. No part of this article promotes usage, distribution, or operational deployment of malware.
EagleSpy in the Modern Mobile Threat Landscape
Within the broader ecosystem of mobile malware, EagleSpy occupies a middle ground between low-effort commodity threats and highly sophisticated state-sponsored spyware. Variants such as EagleSpy v5 demonstrate how Android malware continues to evolve toward improved stealth, persistence, and modular control, making mobile devices an increasingly attractive target for threat actors.
Threat Motivation and Purpose Behind EagleSpy
Threat intelligence assessments suggest that EagleSpy is primarily used for surveillance-driven objectives, including information gathering and long-term monitoring. Its design indicates use by financially or intelligence-motivated actors rather than opportunistic attackers, highlighting a trend toward more targeted mobile malware operations.
How EagleSpy Operates: A General Overview
At a high level, EagleSpy operates by maintaining background execution, monitoring device state, and communicating periodically with remote infrastructure. It is designed to blend into normal system behavior, reducing the likelihood of user suspicion or immediate detection by security tools.
EagleSpy Capabilities Observed in Real-World Samples
Analysis of collected samples shows that EagleSpy variants may support multiple surveillance-related functions, such as activity monitoring and data collection. These capabilities are typically enabled or disabled remotely, reinforcing the malware’s flexibility across different campaigns and targets.
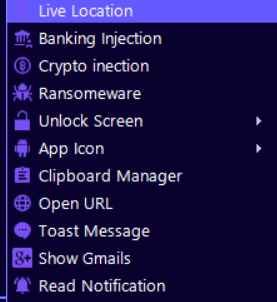
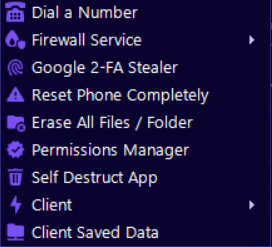
EagleSpy Distribution Methods in Malicious Campaigns
EagleSpy has been associated with common Android malware distribution techniques, including deceptive applications, social engineering, and unofficial app sources. These methods emphasize how user trust and permission abuse remain central to successful mobile attacks.
Post-Infection Behavior of EagleSpy
Once active on a device, EagleSpy focuses on maintaining stability and persistence while minimizing visible indicators. Post-infection behavior often includes background execution, scheduled communication attempts, and conditional activation of specific modules based on attacker intent.
EagleSpy Command-and-Control Infrastructure
Communication between infected devices and attacker-controlled servers is typically encrypted and structured to resemble legitimate traffic. This command-and-control (C2) model enables remote management while complicating network-based detection efforts.
Stealth and Evasion Techniques Used by EagleSpy
EagleSpy incorporates multiple evasion strategies, including delayed execution, permission misuse, and minimal user-facing interaction. These techniques are designed to reduce detection by both users and automated security analysis environments.
Persistence Mechanisms Implemented by EagleSpy
Persistence is a core design goal of EagleSpy. The malware leverages Android system behaviors and permission models to survive reboots and remain active over extended periods, particularly in later variants such as eaglespy v5.
Network Traffic and Behavioral Analysis of EagleSpy
From a network perspective, EagleSpy traffic often appears low-volume and intermittent. Behavioral analysis focuses on identifying unusual communication timing, encrypted payload patterns, and abnormal background activity rather than static indicators alone.
Security Risks Associated With EagleSpy Infections
An EagleSpy infection poses significant risks to device security and data confidentiality. Compromised devices may be subject to long-term monitoring, data exposure, and secondary exploitation, especially when used in sensitive personal or organizational contexts.
Privacy Implications of EagleSpy Activity
EagleSpy directly impacts user privacy by enabling unauthorized data observation and monitoring. The long dwell time commonly associated with such malware increases the potential for extensive privacy violations over time.
Indicators of Compromise (IoCs) Related to EagleSpy
Detecting EagleSpy relies on a combination of behavioral indicators rather than simple signatures. These may include abnormal permission usage, unexplained background services, and suspicious outbound network connections observed during forensic analysis.
Detection Techniques for Identifying EagleSpy
Security teams can improve detection of EagleSpy by combining mobile endpoint protection, behavioral analytics, and traffic inspection. Awareness of evolving variants like eaglespy v5 is critical, as newer versions may alter observable patterns.
Documented Real-World EagleSpy Incidents
Although not as widespread as some Android malware families, EagleSpy has appeared in multiple documented incidents analyzed by independent researchers. These cases highlight its role in targeted campaigns rather than mass distribution.
EagleSpy and CraxsRat Relationship: Shared Codebase and Technical Differences
Threat analysis indicates that EagleSpy is derived from the CraxsRat source code, placing both tools within the same malware family. While they share foundational design elements, EagleSpy—particularly in versions like eaglespy v5—demonstrates improved precision, stability, and operational efficiency, suggesting iterative development and refinement beyond the original codebase.
Prevention and Risk Mitigation Strategies Against EagleSpy
Reducing the risk of EagleSpy infection requires a layered defense approach, including strict application controls, user education, mobile security solutions, and continuous monitoring. Preventive measures remain the most effective defense against surveillance-oriented mobile malware.
Final Assessment and Future Outlook of EagleSpy
EagleSpy represents a broader trend in Android malware evolution toward modular, stealthy, and persistent surveillance tools. As variants such as eaglespy v5 continue to appear, defenders must adapt detection and response strategies to address increasingly subtle mobile threats.




4 Comments
[…] concept of a Telegram RAT represents a shift in how remote access tools can be architected using existing communication platforms rather than traditional server-based […]
[…] architectural patterns have been observed in other Android surveillance frameworks, including EagleSpy, highlighting a broader trend in modular mobile malware […]
[…] from monitoring components. Similar architectural patterns have previously been documented in EagleSpy, particularly in how core functions are isolated for […]
[…] and RAT.s needs […]